I have an ec2 instance on which I'm running a dev server via parcel index.html --host 0.0.0.0 that ultimately listens on 0.0.0.0:1234. Before creating and associating an eip to my instance, I wanted to use the public ip address assoc'd with it and modified my iptables via
sudo iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 1234
This allowed me to visit my server via the browser using the public ip address assoc'd with my ec2 instance and receive the response I expect.
However, I've now created and assoc'd an eip with my instance (because it's a dev server and I start and stop the instance regularly, I want a constant ip address) and although I can continue to ssh into my instance via the eip address, I can't visit the server by using the eip address in my browser.
Since I'm able to ssh to the instance via the eip I wonder if there is some configuration local to the instance that I need to modify to make requests to my server.
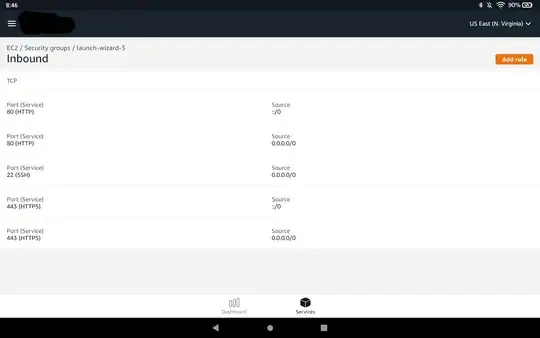
Here are the inbound rules for the security group assoc'd with my instance.