As with most people, we're WFH. It's getting difficult to troubleshoot issues via chat/phone, so we'd like to use the CentOS "Screen Sharing" feature, which comes bundled with the OS, to allow support personnel to connect to user machine's to assist with their issues. The support personnel will also used to built in client vinagre with VNC selected as the connection type.
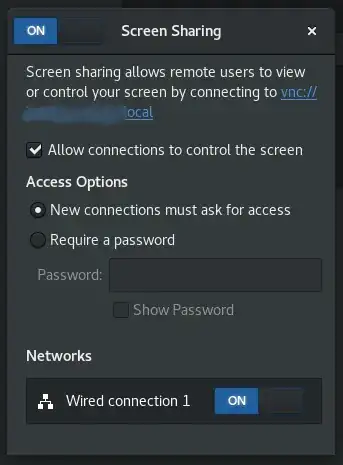
All users are connected to a VPN that is configured to allow internal hosts to communicate with one another. We can ping other hosts, view services they're running, etc. Here is my machine's Screen Share settings.
When I look at netstat, I see port 5900 is listening on tcp6. I considered the issue was the underlying VNC server was listening on IPv6 when every hosts IPv4 interface is set as the default connection, but I recall reading somewhere that tcp6 connections map to tcp4 connections, so it's supposedly a non-issue. Here's my netstat output:
$ sudo netstat -nlt
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:5355 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:10391 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:29754 0.0.0.0:* LISTEN
tcp6 0 0 :::5355 :::* LISTEN
tcp6 0 0 :::5900 :::* LISTEN
tcp6 0 0 :::111 :::* LISTEN
tcp6 0 0 ::1:631 :::* LISTEN
tcp6 0 0 :::9090 :::* LISTEN
I considered it was the firewall, but both my machine and the client machine have firewalld disabled.
Here is the output of nmcli to show the settings of Wired Connection 1
enp57s0u1: connected to Wired connection 1
"Realtek RTL8153"
ethernet (r8152), 8C:04:BA:67:52:16, hw, mtu 1500
ip4 default
inet4 192.168.1.123/24
route4 0.0.0.0/0
route4 192.168.1.0/24
inet6 fe80::xxxx:xxxx:xxxx:xxxx/64
route6 fe80::/64
route6 ff00::/8
Finally, I tested enabling SSH and it worked. Users were able to connect and were prompted to authenticate (we didn't have them actually log-in). This leads me to believe it's an issue with the underlying VNC server itself, something maybe related to it listening on tcp6 above?
Any idea what the issue may be?