Setup
We have an ECS cluster with 2 services (called portal-ECS-service and graph-ECS-service). Each have an ALB (portal-ALB and graph-ALB respectively).
The setup is this:
End user <-> portal-ALB <-> portal-ECS-service <-> graph-ALB <-> graph-ECS-service
Notes
- everything is in the same VPC
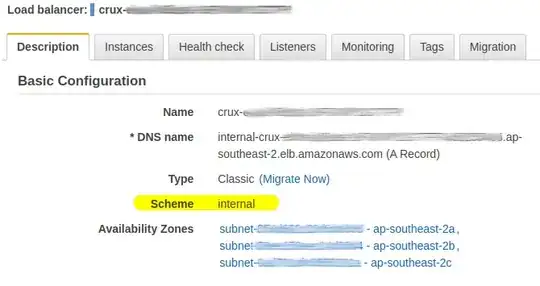
graph-ALBhasScheme: internal- when communicating from
portal-ECS-servicetograph-ALBwe use as the endpointgraph-ALB.us-west-2.elb.amazonaws.com
Problem
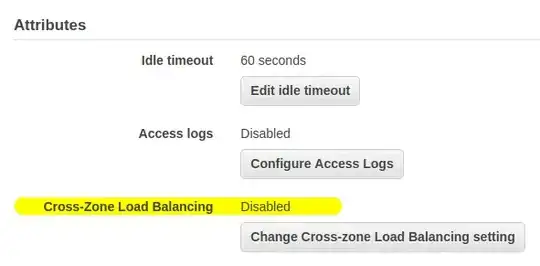
We pay a very large amount (~$50 / day) in DataTransfer-Out-Bytes.
Question
I've read that high DataTransfer-Out-Bytes costs can often be solved by using Internal IP instead of public DNS endpoint.
Is it possible to communicate to an ALB internally without going through the public DNS endpoint? In our case, can we have portal-ECS-service <-> graph-ALB communication without paying high DataTransfer-Out-Bytes costs?
Thank you very much in advance.