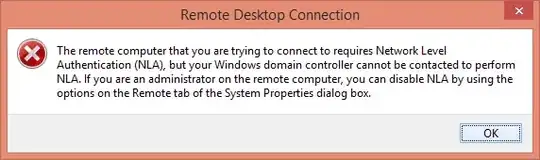
When connecting to a remote PC, I get this error:
But if I walk to the remote PC, login (with the same credentials) and walk back, RDP suddenly works. This happens each day. The remote PC might be powered off in between (I'll check this in the future).
Details:
- remote PC: Windows 10, member of a domain
- client: Windows 10 (not member of domain, at least not the same one)
- used login credentials: a domain user (from the joined domain, obviously)
- time is correct on both (checked with https://time.is)
Walking to the remote PC defeats the purpose of remote access, so I'm looking for help. Also, I would rather not disable NLA.
EDIT:
Another workaround is to use another remote access software, and perform a "local" login (they usually just mirror the local screen and keyboard, so this is possible). After that the RDP login usually works.