Setup
I'm developing for a customer XYZ and have to access APIs running on XYZ Server. We have an IKE2 VPN between our firewalls (XYZ and our office). I am able to ping XYZ Server's Local IP through My Server. We have then created a PPTP VPN so that I can remotely access XYZ's Server. I connected PPTP VPN through Shimo VPN Client on my Macbook, and was able to ping XYZ Server.
Problem
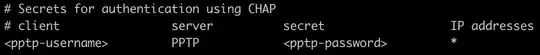
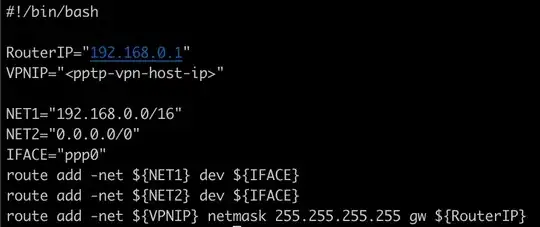
I tried to follow this tutorial (except the iptable config) to create a VPN client on my Ubuntu 18.04 EC2 instance. I think the VPN connects. But I am unable to ping XYZ Server through my EC2 instance. I assume that I have to do some extra config on top of the tutorial to be able to reach XYZ Server. I want that only requests sent to XYZ Server (192.168.102.128) from EC2 to be sent through the VPN connection. What extra config do I need?
EDIT
.
.
syslog: /var/log/syslog
I just realized something. As soon as it says ppp0: Gained carrier my ssh into the server stops responding (seems like instance is rebooting or something). It responds again in a bit with the following added log in syslog.
NOTE: I'm a web developer and not a network engineer. We hired a guy who configured the IKE2 with XYZ. And then exposed it on the pptp VPN. Unfortunately, the guy who configured it for us is not available at the moment. I am able to connect to VPN through 2 of my laptops and then access XYZ's API hosted on XYZ Server (192.168.102.128:7801). I just want the same to happen through ec2 instance (preferably only using VPN for the requests sent to 192.168.102.128).