I'm trying to upload and use a custom SSL certificate and private key which I've generated using my own personal CA I've created.
I've gone through all the steps in their guide to doing so: https://cloud.google.com/appengine/docs/standard/nodejs/securing-custom-domains-with-ssl#converting_private_keys_and_concatenating_ssl_certificates
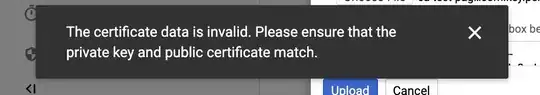
But when I attempt to upload the certificate and key I get the following error:
The certificate data is invalid. Please ensure that the private key and public certificate match.
I've tried a variety of encodings, chain orders, etc but I always get this same error. I don't see anything explicitly calling out that you can have your own custom CA so I'm curious if that's the problem.
The raw HTTP response body I get from the upload API request (console) is the following:
)]}'
{"code":3,"trackingId":"8598058641280346134","errorSpace":"generic","status":400,"message":"backend error"}
Since I'm just doing a dev instance of this for now to ensure it's possible, here's my test certificate chain and private key (THESE ARE NOT USED IN PRODUCTION, I'M POSTING THEM INTENTIONALLY TO HELP DEBUG THIS ISSUE, THEY ARE NOT SENSITIVE DATA):
The certificate chain:
-----BEGIN CERTIFICATE-----
MIID8TCCAtmgAwIBAgIJAL27hhOcC13lMA0GCSqGSIb3DQEBCwUAMGcxCzAJBgNV
BAYTAlVTMRMwEQYDVQQKEwpHcmFudFByb3h5MQswCQYDVQQIEwJDQTEhMB8GA1UE
CxMYR3JhbnRQcm94eSBCcm93c2VyIFByb3h5MRMwEQYDVQQDEwpHcmFudFByb3h5
MB4XDTIwMDQwODIwMzQ1OVoXDTIxMDQwODIwMzQ1OVowWDELMAkGA1UEBhMCVVMx
CzAJBgNVBAgMAkNBMRYwFAYDVQQHDA1TYW4gRnJhbmNpc2NvMSQwIgYDVQQDDBtj
YS10ZXN0LXBhZ2UuZ3JhbnRwcm94eS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IB
DwAwggEKAoIBAQDO1u1pf/MfH3Em7/q6+HINzhyFLgOfLhaOcHBPw+U6jyuD+2BG
KY6QaMiO5bzOSx/CFWQbgKNkKmaLROVs9pAqwDxYtyJkWmcbdyGPfSb0OdNnPo4h
fcKQmEQ6b/5DlPpYojUrwjKnwCTHN55uY1RE4icRFUNWmUkPHWq7hZQGq3gTWc/M
7jgXcaGneOdGL/ABNTZ4gGxb1a1qH/eNQeEIWt+pO9gCaEirjTU5yCps+e7GmIW9
tBypCvyde95eQIBdE+YuC80iAfkDS9uiVfo/DwojZm3GYgukKz3ce6WcmiEhZxBU
8GY6MdZFRLt4RW0WluX1wvBsZ/e8r+k5LfSrAgMBAAGjga4wgaswewYDVR0jBHQw
cqFrpGkwZzELMAkGA1UEBhMCVVMxEzARBgNVBAoTCkdyYW50UHJveHkxCzAJBgNV
BAgTAkNBMSEwHwYDVQQLExhHcmFudFByb3h5IEJyb3dzZXIgUHJveHkxEzARBgNV
BAMTCkdyYW50UHJveHmCAweZATAJBgNVHRMEAjAAMAsGA1UdDwQEAwIE8DAUBgNV
HREEDTALgglsb2NhbGhvc3QwDQYJKoZIhvcNAQELBQADggEBACsM/NktjwF/Euwd
V78g49O2HzC3m4FAKf3xngberQrKBijhfs5DHLn9hrd4p2Go1iUpBRDfc8hmRuhQ
z+HmD5AqEauWyMign0niLlH0FgB9FqE9KdlKmROFpeTZ/c/5GLVY5AAaMLDdC81y
Z2yXxVK67zLNQu9SBosLj5i3Ol4NJDJyHMJV40sNXKpWzN6uhgAuOGki3QDWqvhm
2RpXBN5j7+ug8mdozxtwsWq23STHbcfzNNFmY5vUhaTcL3dgzglRg4Sa65j7veb4
Dh7xqVK86MY9A2IK+seT/4qMCUiK3VDUqxJnVBHgJJuF1HoKYmkEY+kXkrwmkHVk
JIdQavs=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDWzCCAkOgAwIBAgIDB5kBMA0GCSqGSIb3DQEBCwUAMGcxCzAJBgNVBAYTAlVT
MRMwEQYDVQQKEwpHcmFudFByb3h5MQswCQYDVQQIEwJDQTEhMB8GA1UECxMYR3Jh
bnRQcm94eSBCcm93c2VyIFByb3h5MRMwEQYDVQQDEwpHcmFudFByb3h5MB4XDTEw
MDMyOTAwNDU0MloXDTMwMDMyOTAwNDU0MlowZzELMAkGA1UEBhMCVVMxEzARBgNV
BAoTCkdyYW50UHJveHkxCzAJBgNVBAgTAkNBMSEwHwYDVQQLExhHcmFudFByb3h5
IEJyb3dzZXIgUHJveHkxEzARBgNVBAMTCkdyYW50UHJveHkwggEiMA0GCSqGSIb3
DQEBAQUAA4IBDwAwggEKAoIBAQC4j44CfcRjw6J9rl0XqaKCLBdQnMTpwaMGrDH0
2tkBFIDvQw8LMNcFSS+ICYQirAxlFz4ADqN/aspbtlkOdC+2IgsMehQyaaGYEjz6
CmBFExLuf2BpfmnICtnfcNdx0SkZRCx0c2TotgNJLxU985CjP9pxNrOGtt/+J7im
RQzKtPOI9LOPc2iAI7eOJdIe1xgdfHQMV92zD9bxKczW69axUPmDsU0869B3TWAN
md0Zqe0jtll2QsY3DNhPB1cI1TdkwhlW6/EJAdvFL1iI7q8ViSXW/JN2Apfnin9o
KCOERndPsNO+vYKlikkgOdUb40UCd+rKCdP2i7PjvpJtSQRNAgMBAAGjEDAOMAwG
A1UdEwQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAJusJqC9pcnoolqRYf0h6sW8
rekD/vdj3BMZvH//ZQcvfOOx81FI99+wKMe/H3l7E8pjZbwW4SXcT7QYT96QGYrQ
qY8sAVNG3009oneKTjPdtwO+0nDbcmgFqEOXSf3zZBC6NeiufL51zJJFCliVPUBM
ETzJoYsazmF4xcPXx9iOn+2vYvB/w7rDcEbY+ccJ0yyJpppnUeOXgX1btX/OVi1A
DFx/GUpaZ8GDDwVv5G87nbgtAJUxTHZrMrxOQF3oFZOsyidpMr4V3lQ8O+Vq/fBu
EkRZdxxEC3cDDtlSQHyQ+jelQKskuEUr7n2X3CMU6B2qGyY7Q3NYuBGrUCK9hac=
-----END CERTIFICATE-----
The private key for the server:
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAztbtaX/zHx9xJu/6uvhyDc4chS4Dny4WjnBwT8PlOo8rg/tg
RimOkGjIjuW8zksfwhVkG4CjZCpmi0TlbPaQKsA8WLciZFpnG3chj30m9DnTZz6O
IX3CkJhEOm/+Q5T6WKI1K8Iyp8AkxzeebmNUROInERVDVplJDx1qu4WUBqt4E1nP
zO44F3Ghp3jnRi/wATU2eIBsW9Wtah/3jUHhCFrfqTvYAmhIq401OcgqbPnuxpiF
vbQcqQr8nXveXkCAXRPmLgvNIgH5A0vbolX6Pw8KI2ZtxmILpCs93HulnJohIWcQ
VPBmOjHWRUS7eEVtFpbl9cLwbGf3vK/pOS30qwIDAQABAoIBADg4GN2FBnreG+4+
agLpxm5UKFJWmGtqpnzeuNglYafSBDziVV+cqgA8Ss70SKY1qxMgp04GX+K415hh
CI7eUX8dMwnV9QYbwEypy7hphu34zaoRSaZ2vSx6BolvqUeLNaRjqloTdZs80YJI
bsqIOv5iDcZJ5jyie0Ydc8Y2X26ULSZXzAjLpBsr2QJthe/4SZBxOVw93HFjNh3q
9AfTRzvcEKIA5vTzMihCLroH5ou7xY331qnHiCWhHNReLpU6wNfjAoHGDPQv69Gf
yX7xyMG1Kb5bMjqepMVu/2a7aU5/PC/ia9VpIH6yeRYQoP4AioFfE4HWZtg0CuSb
D7izKPkCgYEA99xM6pq26P2FlhBT9SWlR+FnFtSaeZiuC3KErj1Y/RQCnKHX2gC2
At1XIW3S6TzRaMieSLbDl7wbuuKNs9o7FE4n8kN7iS1kTWlV+eFyTkiAkWeJi2W3
Ksket/5qW5mSUauoCyKhnr5rOSgpywDSwCjBbNbwIPNiWFmtVqrkLV8CgYEA1aHG
KudnDXgdG2jU5CLz66VDIAHXew7tLSr/h0y6q7d6IOGSSJF3iOKg1/cI68TeyxgZ
al/wiOAY2xFGOJu3CeuZPS93jOM6Z/YPEssAvDmAEJrLeNJGt7HKpW5jm9DduIHE
MrariM/SK+pzH0erWXmPU9PZOYaiJ+gtYWxJcDUCgYEAw5UA1LcU0jELMmjb9zun
elrwv+Evq/fAjqPk8qDSEZGypepHq2yYMxZ5ZJWGsikdjTORQwuEt7zlnMiczGjN
6a3qc46wcoRw+2y9PRqa2g739MTgkjDHImnlZYbKYlGCVhO/3FmNcvgLH+UDZX7W
zm7agonwne+vkMvirdrXhr0CgYA6LRbhIikPIvGSQEcRZW9VcajI85dxnIv8K+Rw
PPXsw0dP4v3KI0sRDN5OUaitQ+yEFCj/rea774L1TUv5KHZ9Dhqp7d45kLucCgbq
0DuABoyYeP8GBQVbCuCrklcv3H40u6npQZOO60FJ0kvNbd/8urzMUDmsj7xi77hD
+pA5LQKBgQDzfT+YDhp6ERxgnj18gjh7bQIFlGobvf9DTy6F+yhvLYWCPfOOo5do
evKlFnUyNwtcTY0zCko4Tr7yvm6Dfwb/vrCPdLcC/GJJOR8wtRLIs5A18kZNNVF5
wBvGH6PqufGWqbToJwaXFFrhIJl0wsKnreTqxuPnDRwu8ExnbNMRbQ==
-----END RSA PRIVATE KEY-----