I use a mixture of Windows, Linux, and Macs and have noticed big differences in how each OS shows certificate details using the default tools available in each.
The way Windows displays certificate details is very succinct. Specifically, the certificate chain. See screenshot as an example.
 And here it is again in Windows, but using the
And here it is again in Windows, but using the certutil tool. (okay it's inspecting a pfx but you get the point).
 However on a Mac, this is how it shows the same cert in
However on a Mac, this is how it shows the same cert in Keychain Access.
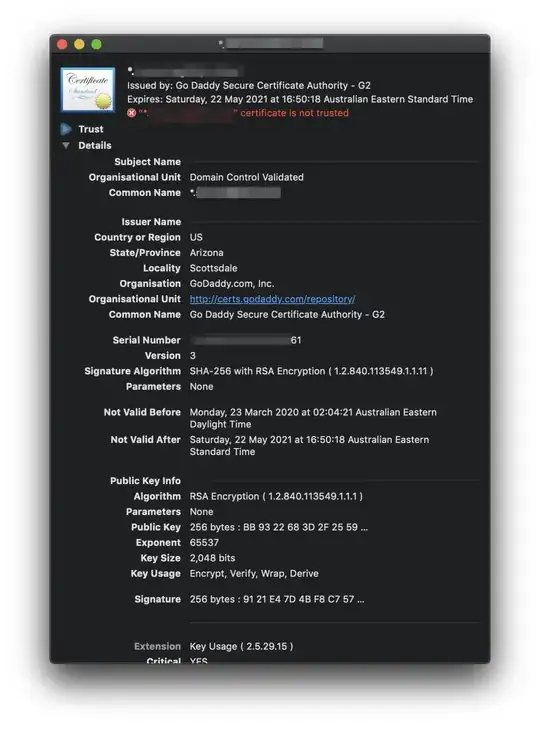 As you can see, it doesn't have a nice hierarchical view that makes it easy to identify the certificate chain that Windows or
As you can see, it doesn't have a nice hierarchical view that makes it easy to identify the certificate chain that Windows or certutil shows - at least not to my (possibly) untrained eyes.
I also haven't figured out a way to show the certificate chain using openssl either, for example, the following command openssl x509 -in certificate.crt -text does not show a hierarchical chain - only the issuer.
So is there a way to view a certificate's chain whether it be text or an image using openssl or native Mac tools?
[Edit]:
I often create PFX files with the entire certificate chain (bar the root) for distribution within the company I work for. As part of the process I double check that the certs I've downloaded from the issuing CA are correct and that they're in the right order before passing it to openssl to mint the PFX. So to be clear, I'm questioning how to view the chain of a certificate I am working on locally on my computer.