the question is very similar to the one posted here: Routing via gateway to another subnet
My question is about the correct routing / iptable settings for the following network topology, which includes a site-to-site VPN between site-A and site-B.
The client-A wants to access client-B, for instance a webserver is hosted on client-B. For simplicity I want to focus on site-A only. Let us assume that client-B has vpn-server-B as its gateway.
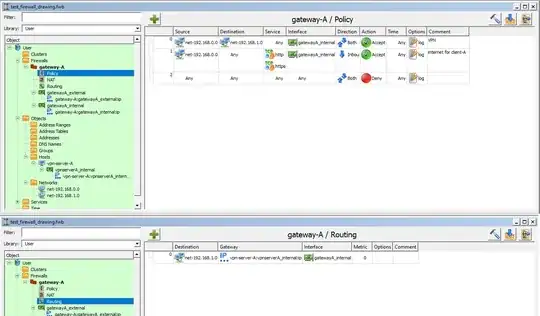
client-A can access the webserver on client-B, if client-A uses vpn-server-A as its gateway. But client-A also wants to access the internet via the gateway. Therefore, client-A sets gateway-A as its default gateway. So gateway-A should forward the traffic for 192.168.1.0/24 to vpn-server-A. I use firewall builder in order to configure the firewall and routing rules. I set up the following in firewall builder.
client-A can ping successfully client-B but no http(s) conection can be established. Having a look into the log file of gateway-A:
Apr 3 21:22:35 gateway-A kernel: [ 5456.799769] RULE 1 -- ACCEPT IN=eth0 OUT=eth0 MAC=00:11:22:33:44:55:00:55:44:33:22:11:08:00 SRC=192.168.0.100 DST=192.168.1.100 LEN=52 TOS=0x02 PREC=0x00 TTL=127 ID=28583 DF PROTO=TCP SPT=53133 DPT=443 WINDOW=8192 RES=0x00 CWR ECE SYN URGP=0
Apr 3 21:22:35 gateway-A kernel: [ 5456.814869] RULE 3 -- DENY IN=eth0 OUT=eth0 MAC=00:11:22:33:44:55:00:55:44:33:22:11:08:00 SRC=192.168.0.100 DST=192.168.1.100 LEN=40 TOS=0x00 PREC=0x00 TTL=127 ID=28584 DF PROTO=TCP SPT=53133 DPT=443 WINDOW=260 RES=0x00 ACK URGP=0
The problem seems to be that the gateway-A does not redirect correctly the traffic to the vpn-server-A. As the last comment in the post linked above one should check the firewall. Probably an additional NAT is required but I do not understand why. The incoming request to access 192.168.1.0/24 at gateway-A should be just redirected to vpn-server-A.