As I was auditing an org's AWS IAM, I did:
aws iam generate-credential-report
# a bit later, download the CSV
aws iam get-credential-report
During viewing the report, one thing struck me as highly unusual: the column password_last_used for <root_account> is not empty value:
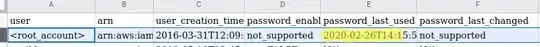
How is this even possible?
IAM root accounts are supposed to be passwordless; even in this report, password_enabled shows not_supported.
What're the implications of this datum? Could this be an indication of breach?
Is this some kind of known AWS glitch? Whom should I email to clear this up?