This is my first time setting up VLANs on a Cisco so I've probably made some mistakes - would appreciate some suggestions. Thank you in advance.
...
From my understanding of switches, when a layer 2 broadcast packet is received, the switch should send it out to all other ports within the broadcast domain except the originating port.
Without VLANs, the broadcast domain should be all physical ports. If those ports are attached to switches, then those switches would in turn replicate it to all other ports as well.
In a VLAN setup, the broadcast domain is all physical ports that are "configured" to use that VLAN.
Note: Technically "interfaces" .. and "tagged" are correct terminology but I'm being careful not to use words that can mean different things with different vendors.
So if my understanding is correct, then something seems to be preventing broadcast traffic from being sent to all other ports. I've used a packet sniffer on the router to determine this. There are no received packets on the specific interface with a destination mac address of ff:ff:ff:ff:ff:ff:ff:ff.
My physical setup is this:
Cisco SG500-52MP switch. Three ports are configured for VLAN #14. In Cisco language these are configured as "Access Ports". My understanding of that is that it means all ingress traffic is tagged to VLAN 14. All egress traffic is untagged. When I say "tagged", I mean the VLAN id is added to the packet, and untagged means its stripped.
Of those three ports, one connects to a PC, one to a controller, and one to the Mikrotik Router. The interface on the router has no VLAN configuration at all - the ports aren't bridged - its functioning as an actual router.
On the Cisco switch, when I do "show vlan" it shows me:
`Vlan Tagged Ports UnTagged Ports ---- ------------ -------------- 1 gi1/23-24,gi1/31-47,gi1/49-52,po1-32 10 14 gi1/25-30 32 gi1/49 gi1/1-22,gi1/48 200 gi1/50
Interfaces 27-29 have the same switchport configuration.
show interfaces switchport ge1/1/27
Added by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, T-Guest VLAN, V-Voice VLAN
Port : gi1/27
Port Mode: Access
Gvrp Status: disabled
Ingress Filtering: true
Acceptable Frame Type: admitAll
Ingress UnTagged VLAN ( NATIVE ): 14
Port is member in:
Vlan Name Egress rule Added by
---- -------------------------------- ----------- ----------------
14 BMS Untagged S
Forbidden VLANS:
Vlan Name
---- --------------------------------
Classification rules:
Protocol based VLANs:
Group ID Vlan ID
------------ -------
Mac based VLANs:
Group ID Vlan ID
------------ -------
I notice it says "Ingress Filtering: true" .. My understanding is that should not filter out packets without a VLAN identifier (VLan #1 in Cisco language), since its an access port.
show run int ge1/1/29
interface gigabitethernet1/29
switchport mode access
switchport access vlan 14
!
Also - the version ... show version
SW version 1.4.11.2 ( date 26-Sep-2019 time 20:01:21 )
Boot version 1.3.5.06 ( date 21-Jul-2013 time 15:12:21 )
HW version V03
When I use the router's packet sniffer tool on the specific port for this VLAN, I can only see multicast packets between the switch and the router .. and one lone discovery packet from the router. It very clearly shows that no packets are received with a VLAN ID - which is what I expect.
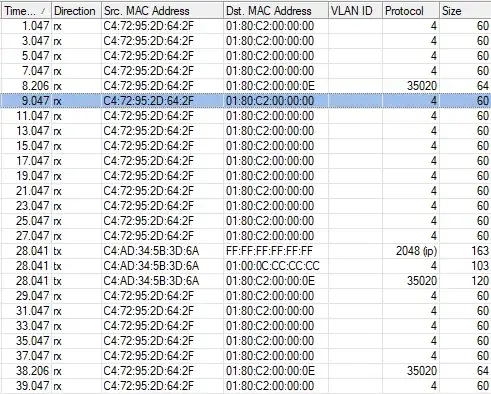
When I do a packet sniff while trying to ping the static IP of the controller host, I can see the ARP requests leaving the router correct, but nothing being received.
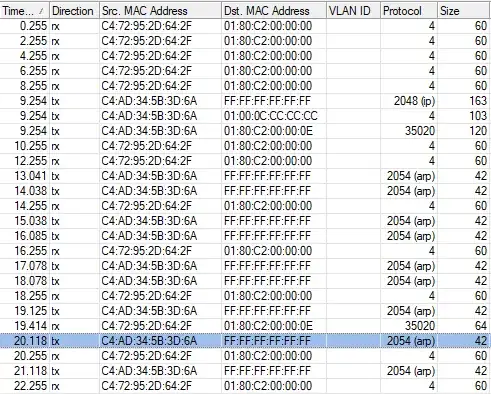
Previously I took another small Mikrotik and hooked it into one of the three ports on the cisco and did a packet capture on the receiving end. The ARP packets did not make it through.
So this tells me the Cisco is filtering them .. but why? I should add that when I configured these switches, I did a complete factory reset, and then copied / pasted the configuration commands I had saved. This is my way of ruling out any sort of typos, or referencing the wrong interface by accident. I know these Small Business switches have some nuances to them vs the Catalysts - and something tells me I'm being bit by one of them.