Client(React Js) - @azure/msal-react, @azure/msal-browser Server(Express Js) - Passport-azure-ad
var options = {
identityMetadata:"https://login.microsoftonline.com/<tennant-id>/v2.0/.well-known/openid-configuration",
clientID:"<client-id>",
validateIssuer:true,
issuer: "https://login.microsoftonline.com/<tennant-id>/v2.0",
passReqToCallback: false,
allowMultiAudiencesInToken: false,
audience:"<client-id>",
loggingLevel: "info",
loggingNoPII: false,
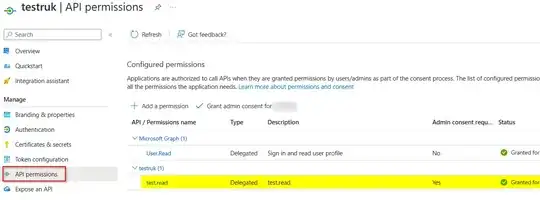
scope: ["User.Read"],
};
var bearerStrategy = new BearerStrategy(options,
function(token, done) {
log.info('verifying the user');
log.info(token, 'was the token retreived');
findById(token.oid, function(err, user) {
if (err) {
return done(err);
}
if (!user) {
// "Auto-registration"
log.info('User was added automatically as they were new. Their oid is: ', token.oid);
users.push(token);
owner = token.oid;
return done(null, token);
}
owner = token.oid;
return done(null, user, token);
});
}
);
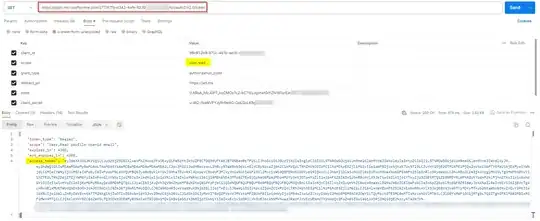
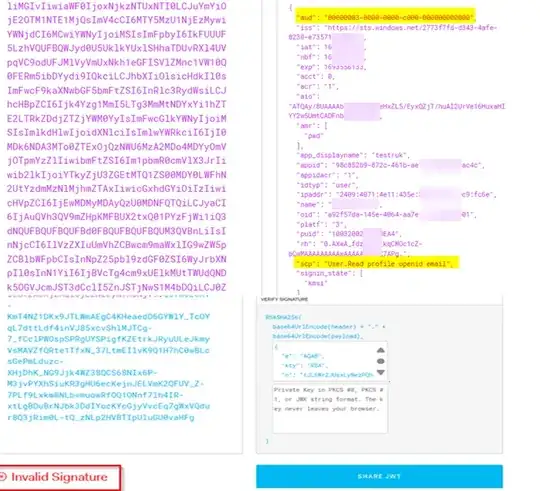
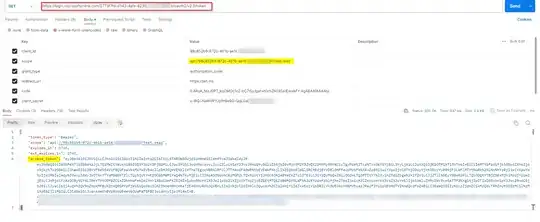
Error log - {"name":"AzureAD: Bearer Strategy","hostname":"xxxxx-xxxxx","pid":xxxxx,"level":x,"msg":"authentication failed due to: invalid signature","time":"xxxx","v":0}
Though the server receives the accessToken from the client in Headers as Authorization Bearer Token to which it parses and also decodes the token to provide the userInfo. But after generating the pemKey I get the above error log.
What could be the reason for this error log.
Any help is appreciated, thanks