I have the following cloudformation template it is creating the ec2 instance properly but not able to connect to the ec2 instance with either instance connect or ssh from putty. I have seen other answers suggesting to attach internet gateway to the subnet , I have done that it still does not work:
{
"AWSTemplateFormatVersion": "2010-09-09",
"Metadata": {
"AWS::CloudFormation::Designer": {
"60dcb39c-cc02-4b3a-bc24-159bb4641b6d": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 150,
"y": 90
},
"z": 1,
"embeds": [],
"iscontainedinside": [
"f249024f-80d9-4123-8e23-c94b2a3369bc"
]
},
"27de666e-5af9-44ee-bfa5-67e48f8cce27": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 240,
"y": 90
},
"z": 1,
"embeds": [],
"iscontainedinside": [
"0c56b978-8a45-40dc-9691-635296a3fa7e"
]
},
"f249024f-80d9-4123-8e23-c94b2a3369bc": {
"size": {
"width": 90,
"height": 90
},
"position": {
"x": 360,
"y": 90
},
"z": 1,
"embeds": []
},
"0c56b978-8a45-40dc-9691-635296a3fa7e": {
"size": {
"width": 90,
"height": 90
},
"position": {
"x": 930,
"y": 150
},
"z": 1,
"embeds": []
},
"7ca9ec38-462f-4daa-be8e-3360b3396a7b": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 270,
"y": 210
},
"z": 1,
"embeds": []
},
"45db66a4-341b-4870-90e9-408effaccabd": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 420,
"y": 270
},
"z": 1,
"embeds": []
}
}
},
"Resources": {
"vpc1": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": "70.70.0.0/16",
"EnableDnsSupport": "true",
"EnableDnsHostnames": "true"
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "0c56b978-8a45-40dc-9691-635296a3fa7e"
}
}
},
"subnet1": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"VpcId": {
"Ref": "vpc1"
},
"CidrBlock": "70.70.0.0/24",
"MapPublicIpOnLaunch": true,
"AvailabilityZone": "ap-south-1a"
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "f249024f-80d9-4123-8e23-c94b2a3369bc"
}
}
},
"secGrp1": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupName": "secGrpNm",
"GroupDescription": "secGrpDesc",
"VpcId": {
"Ref": "vpc1"
},
"SecurityGroupIngress": [
{
"IpProtocol": "tcp",
"FromPort": 8080,
"ToPort": 8080,
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": 22,
"ToPort": 22,
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"IpProtocol": "-1",
"CidrIp": "0.0.0.0/0",
"Description": "Allow all traffic"
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "27de666e-5af9-44ee-bfa5-67e48f8cce27"
}
}
},
"ec2": {
"Type": "AWS::EC2::Instance",
"Properties": {
"ImageId": "ami-0376ec8eacdf70aae",
"InstanceType": "t2.micro",
"AvailabilityZone": "ap-south-1a",
"KeyName": "kipee",
"IamInstanceProfile": {
"Ref": "instanceProfile1"
},
"NetworkInterfaces": [
{
"AssociatePublicIpAddress": "true",
"DeviceIndex": "0",
"SubnetId": {
"Ref": "subnet1"
},
"GroupSet": [
{
"Ref": "secGrp1"
}
]
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "60dcb39c-cc02-4b3a-bc24-159bb4641b6d"
}
}
},
"instanceProfile1": {
"Type": "AWS::IAM::InstanceProfile",
"Properties": {
"Path": "/",
"Roles": [
{
"Ref": "role1"
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "7ca9ec38-462f-4daa-be8e-3360b3396a7b"
}
}
},
"ig1": {
"Type": "AWS::EC2::InternetGateway",
"Properties": {}
},
"gateway1": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"VpcId": { "Ref": "vpc1" },
"InternetGatewayId": { "Ref": "ig1" }
}
},
"role1": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"Path": "/",
"Policies": [
{
"PolicyName": "XrayWriteOnlyAccess",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"xray:PutTraceSegments",
"xray:PutTelemetryRecords",
"xray:GetSamplingRules",
"xray:GetSamplingTargets",
"xray:GetSamplingStatisticSummaries"
],
"Resource": "*"
}
]
}
}
]
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "45db66a4-341b-4870-90e9-408effaccabd"
}
}
}
}
}
Below is the event log while for the stack:
I am getting timeout error when connecting with the keypair in putty:
And this is the instance connect error:
Update 1:
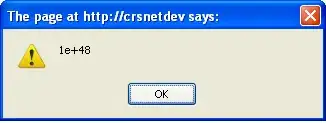
I added network Act in cloud formation and the error changed but I am still not able to connect :
"netAcl1": {
"Type": "AWS::EC2::NetworkAcl",
"Properties": {
"VpcId": { "Ref": "vpc1" },
"Tags": [
{ "Key": "Name", "Value": "netAcl1" }
]
}
},
"MyNetworkAclInboundRule": {
"Type": "AWS::EC2::NetworkAclEntry",
"Properties": {
"NetworkAclId": { "Ref": "netAcl1" },
"RuleNumber": 100,
"Protocol": "6",
"RuleAction": "allow",
"CidrBlock": "0.0.0.0/0",
"Egress": false,
"PortRange": {
"From": 22,
"To": 22
}
}
},
"MyNetworkAclOutboundRule": {
"Type": "AWS::EC2::NetworkAclEntry",
"Properties": {
"NetworkAclId": { "Ref": "netAcl1" },
"RuleNumber": 100,
"Protocol": "6",
"RuleAction": "allow",
"CidrBlock": "0.0.0.0/0",
"Egress": true,
"PortRange": {
"From": 22,
"To": 22
}
}
}
The new error is: