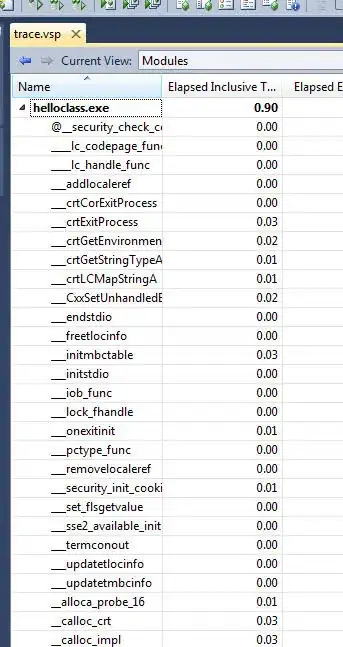
I would like to be able to create a SAS Token on a Datalake folder in a very specific manner using Powershell. I am able to create the SAS Token in the Azure Portal and cannot find a way to create it exactly like that in Powershell.
The SAS Token has to fullfill these conditons:
- Permit access to a Datalake directory
- Use an Access Policy
- The Access Policy does not provide Start Time or Expiry Time
- The Access Policy does not provide Permissions
- The SAS Token itself provides Start Time and Expiry Time
- The SAS Token itself provides Permission
I used the existing storage account "gfcssa002t" and created a Datalake container "datalake".
Within this container I created a the folder structure "basefolder/testfolder" and uploaded a file "testfile.png":
In the next step I created an Access Policy "testpolicy" with no permission, no start time and no exiry time:
Now I was able to start generating a SAS Token for the folder "basefolder/testfolder":
I generated a SAS Token using Account Key signing (key1), the Access Policy "testpolicy", 5 Permissions (Read, Add, Create, Write, List), Start Time "01.01.2023 00:00:00" and Expiry Time "01.01.2024 00:00:00":
I copied the generated SAS Token URI, inserted "/testfile.png" just behind the part "/datalake/basefolder/testfolder" within the URI, opened a new private Firefox window and inserted this URI:
So, the SAS Token worked the way I expected.
Now I tried to do the same generation of SAS Token by Powershell. Unfortunatly it is not that easy to find out which cmdlet to use. For me it seemed the best to use the cmdlet New-AzStorageBlobSASToken (Documentation) using the code:
$accountname="gfcssa0002t"
$accountkey="<.. key ..>"
$containername="datalake"
$blob="basefolder/testfolder"
$policy="testpolicy"
$ctx = New-AzStorageContext -StorageAccountName $accountName -StorageAccountKey $accountKey
New-AzStorageBlobSASToken `
-Context $ctx `
-Container $containername `
-Blob $blob `
-Policy $policy `
-Protocol HttpsOnly `
-FullUri
But this one only works if you define at least Permissions for the Access Policy "testpolicy". If I do not define Permission, Start Time, Expiry Time I get the error
New-AzStorageBlobSASToken : Der Wert darf nicht NULL sein.
Parametername: accessPolicy
In C:\Users\...\Projects\Create SAS token.ps1:10 Zeichen:1
+ New-AzStorageBlobSASToken `
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (:) [New-AzStorageBlobSASToken], ArgumentNullException
+ FullyQualifiedErrorId : ArgumentNullException,Microsoft.WindowsAzure.Commands.Storage.Blob.Cmdlet.NewAzureStorageBlobSasTokenCommand
The same error occurs, when I add Start Time and Expiry Time to the cmdlet:
$accountname="gfcssa0002t"
$accountkey="<.. key ..>"
$containername="datalake"
$blob="basefolder/testfolder"
$policy="testpolicy"
$ctx = New-AzStorageContext -StorageAccountName $accountName -StorageAccountKey $accountKey
New-AzStorageBlobSASToken `
-Context $ctx `
-Container $containername `
-Blob $blob `
-Policy $policy `
-Protocol HttpsOnly `
-StartTime (Get-Date).AddDays(-1) `
-ExpiryTime (Get-Date).AddDays(10) `
-FullUri
And if I try to use the parameter "Permission":
$accountname="gfcssa0002t"
$accountkey="<.. key ..>"
$containername="datalake"
$blob="basefolder/testfolder"
$policy="testpolicy"
$ctx = New-AzStorageContext -StorageAccountName $accountName -StorageAccountKey $accountKey
New-AzStorageBlobSASToken `
-Context $ctx `
-Container $containername `
-Blob $blob `
-Policy $policy `
-Protocol HttpsOnly `
-StartTime (Get-Date).AddDays(-1) `
-ExpiryTime (Get-Date).AddDays(10) `
-Permission racwl `
-FullUri
The error changes to:
New-AzStorageBlobSASToken : Der Parametersatz kann mit den angegebenen benannten Parametern nicht aufgelöst werden.
In C:\Users\...\Projects\Create SAS token.ps1:10 Zeichen:1
+ New-AzStorageBlobSASToken `
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (:) [New-AzStorageBlobSASToken], ParameterBindingException
+ FullyQualifiedErrorId : AmbiguousParameterSet,Microsoft.WindowsAzure.Commands.Storage.Blob.Cmdlet.NewAzureStorageBlobSasTokenCommand
According to the documentation of the cmdlet there seems to be no valid set of parameters to use an Access Policy, Start Time, Expiry Time and Permission together.
And that's the point where I ran out of ideas.
How do I achieve the generation of the exact same kind of SAS Token I was able to create with Azure Portal?