I'm trying to setup an Azure SQL database using P2S VPN for users who are remote working. They are using some applications like SSMS and Visual Studio that require access to the database. We allow them to connect by white listing their IP addresses but we would like to stop this and to use the deny public network access option on the SQL server on Azure.
Whenever I try to connect using SSMS I get the following message:
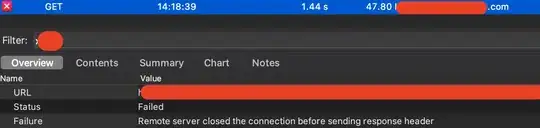
I've followed the steps outlined in the documentation and tutorials on MS Docs but I have not been able to get the private endpoint to work with the database.
I have created the virtual network gateway and connected it to Azure Active Directory and I can see the sessions being created by the users as they log in.
I have created the virtual network using the address range = 10.1.0.0/16 and the subnet address range = 10.1.0.0/24. I have attached the private endpoint connection to the Azure SQL server and added the virtual network to the firewall.
Is there some setting required to allow the user to connect to the database from their PC without whitelisting IP addresses?