I realize this is a very old thread, but there's something in here that I just found out is potentially misleading.
"3. Configure the server(s) to force all incoming connections to use SSL so that any clients that do not support this will fail to connect. In SQL Server Configuration Manager, set the ForceEncryption parameter to "Yes" in the Protocols section."
The ForceEncryption parameter on the SQL server side does not fail clients that do not have Encrypt = True set on the client end. Importantly, you can create insecure connections to the SQL server instance even when ForceEncryption is set to "Yes" on the server.
You can validate this by setting ForceEncryption = Yes on the server side, then by connecting to that SQL server using SSMS and choosing not to encrypt the connection on the client side.
You can check the encryption state of the client connection by visiting the Properties of the server in Object Explorer, then clicking on View Connection Properties (right click on the servername in Object Explorer, then click Properties).
You can then see that the value for the Encypted property is set to No.
You can then do a select or other SQL statement to confirm that you are able to access data from the server side, without encryption. I believe that in order to have full end-to-end encryption, you must set encryption on both the client and the server side.
Here is a Microsoft link explaining this issue.
And a screenshot in case that link doesn't work.
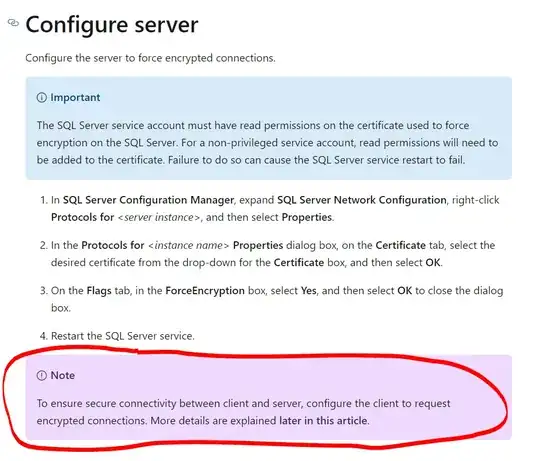
And another Microsoft link saying the same thing.
And another screenshot in case that link doesn't work.



