I'm working on a Django application which needs to support LDAP authentication directly into default admin page.
I've integrated django-auth-ldap and followed the documentation until i could understand it.
I've already configured a local LDAP server using OpenLDAP and a php graphic interface (i'm also able to use ldif file configuration). When i try login into Admin page, Django finds the local server and the user objects inside of it, and also recognizes to which group a user belongs. Despite this i'm not able to login. The error i find:
[21/Aug/2014 11:06:53] "GET /admin/ HTTP/1.1" 200 1870
search_s('ou=users,dc=whiteqube', 2, '(cn=%(user)s)') returned 1 objects: cn=sonia,ou=users,dc=whiteqube
DEBUG:django_auth_ldap:search_s('ou=users,dc=whiteqube', 2, '(cn=%(user)s)') returned 1 objects: cn=sonia,ou=users,dc=whiteqube
Authentication failed for sonia
DEBUG:django_auth_ldap:Authentication failed for sonia
[21/Aug/2014 11:06:56] "POST /admin/ HTTP/1.1" 200 2046
In the Admin interface, just fail to login.
My settings.py:
# - - - - LDAP CONFIGURATION - - - - #
#
# Importing ldap libraries and applications
import ldap
from django_auth_ldap.config import LDAPSearch, GroupOfNamesType, PosixGroupType
# ...connecting to ldap server (local environment uses IP)
AUTH_LDAP_SERVER_URI = "ldap://10.0.2.15"
# ...account to enter into ldap server (anonymous is not always allowed)
#AUTH_LDAP_BIND_DN = "cn=admin,dc=whiteqube"
#AUTH_LDAP_BIND_PASSWORD = "root"
# ...path where to start to search groups
AUTH_LDAP_GROUP_SEARCH = LDAPSearch("ou=groups,dc=whiteqube",
ldap.SCOPE_SUBTREE, # allow searching from current node to all nodes below
"(objectClass=posixGroup)" # type of object
)
AUTH_LDAP_GROUP_TYPE = PosixGroupType() # a posixGroup is identified by the keyword "cn" into ldap server
# ...associations between ldap and django groups
AUTH_LDAP_USER_FLAGS_BY_GROUP = {
"is_active": "cn=active,ou=groups,dc=whiteqube",
"is_staff": "cn=staff,ou=groups,dc=whiteqube",
"is_superuser": "cn=superuser,ou=groups,dc=whiteqube"
}
AUTH_LDAP_PROFILE_FLAGS_BY_GROUPS = {
"is_awesome": ["cn=awesome,ou=groups,dc=whiteqube"]
}
# ...node where to start to search users
AUTH_LDAP_USER_SEARCH = LDAPSearch("ou=users,dc=whiteqube",
ldap.SCOPE_SUBTREE, # allow searching from current node to all nodes below
"(cn=%(user)s)"
#"(objectClass=posixAccount)"
#"(objectClass=inetOrgPerson)"
)
# Keep ModelBackend around for per-user permissions and maybe a local
# superuser.
AUTHENTICATION_BACKENDS = (
'django_auth_ldap.backend.LDAPBackend',
'django.contrib.auth.backends.ModelBackend',
)
# Enable debug for ldap server connection
logger = logging.getLogger('django_auth_ldap')
logger.addHandler(logging.StreamHandler())
logger.setLevel(logging.DEBUG)
# - - - - END LDAP CONFIGURATION - - - - #
My LDAP is filled with these objects:
- ou=groups,dc=whitecube
- cn=superuser,ou=groups,dc=whiteqube
- cn=staff,ou=groups,dc=whiteqube
- ou=users,dc=whiteqube
- cn=sonia,ou=users,dc=whiteqube
where "groups" and "users" are OrganizationalUnit, "staff" and "superuser" are posixGroup, "sonia" is a posixAccount.
view the picture for the
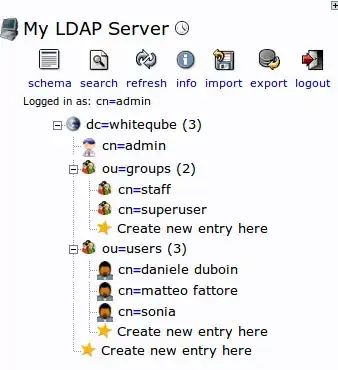
I'm sure ldap objects are configured as must, inasmuch as Django debug recognizes user's group dependace.
Ps: i'm able to login admin when i use a django local account.
Where am I mistaking? Are there any further attributes configuration i missed?